Amazon S3 – Security Features and Encryption
Day 7-Part 2: Prep- AWS Certified Cloud Practitioner | CLF-C02
Introduction
Amazon S3 (Simple Storage Service) provides robust security features to protect your data, including encryption at rest and in transit, access control lists (ACLs), bucket policies, and integration with AWS Identity and Access Management (IAM) for granular access control.
User-Based Security:
IAM (Identity and Access Management):
IAM allows defining policies for specific users or roles.
Users or roles with IAM permissions can access S3 objects.
Access can be granted directly through IAM policies or indirectly through resource policies attached to the S3 bucket.
IAM controls user actions within S3, such as uploading files or modifying settings.
If there's an explicit "DENY" statement blocking access, it overrides any allowed permissions.
Resource-Based Security:
Resource policies in Amazon S3 determine who can access the resources (like buckets and objects) within the service.
They set the rules for IAM (Identity and Access Management) principals, which include users, groups, and roles within your AWS account, as well as for other AWS accounts outside of yours.
These policies specify permissions for accessing and interacting with S3 resources, providing control over data access at both the bucket and object levels.
a) Access Control Lists
Object Access Control Lists (ACLs): Fine-grained control over individual objects within a bucket.
Bucket Access Control Lists (ACLs): Setting broader access controls for the entire bucket.
b) Bucket Policies:
Bucket policies are rules applied at the bucket level in Amazon S3.
They define access permissions for the entire bucket.
They provide granular control over access to data stored within the bucket.
For example, a bucket policy can grant public access to objects for hosting a website or allow cross-account access to share resources.
Access is granted according to the policy unless there's an explicit "DENY" statement blocking it.
S3 Bucket Policies Overview:
Format: JSON-based.
Resources: Buckets and objects.
Effect: Allow or Deny access.
Actions: Set of API operations.
Principal: Specifies the account or user.
S3 Bucket Policies Use Cases:
This table summarizes various scenarios and use cases related to S3 bucket policies and IAM permissions for accessing and securing data stored in Amazon S3.
| S3 Bucket Policies Use Cases | Scenario | Example | Use Case |
| Public Access - Bucket Policy | Hosting a public website. | Granting "s3:GetObject" permission to all users for objects in the bucket. | Making website files accessible to the public. |
| User Access to S3 - IAM Permissions | Granting specific users access to a bucket. | Assigning "s3:PutObject" and "s3:GetObject" permissions to a development team. | Allowing developers to upload and download files for a project. |
| EC2 Instance Access - IAM Roles | Allowing EC2 instances to access S3. | Attaching an IAM role to an EC2 instance with permissions to access a specific bucket. | Enabling an application running on an EC2 instance to retrieve files from S3. |
| Cross-Account Access - Bucket Policy | Sharing resources across AWS accounts. | Allowing read-only access to objects in a bucket for a specific account. | Providing access to resources stored in S3 to a separate AWS account. |
| Force Encryption at Upload | Ensuring data is encrypted when uploaded to S3. | Enforcing server-side encryption with S3-managed keys (SSE-S3) for all uploads. | Protecting data confidentiality by encrypting it before storage in S3. |
Bucket settings for Block Public Access
Prevent Public Access: Block Public Access settings in Amazon S3 help prevent accidental exposure of data to the public internet.
Granular Control: These settings offer options to block public access to bucket policies, access control lists (ACLs), and enforce restrictions account-wide.
Options Included: The settings include blocking new bucket policies and ACLs that grant public access, ignoring existing public ACLs, and blocking public and cross-account access.
Default Setting: You can set Block Public Access as the default for all new buckets, ensuring consistent security practices.
Override Consideration: While strong, these settings can be overridden by specific permissions granted through IAM policies or bucket policies explicitly allowing public access.
Verification and Monitoring: Regularly review and monitor Block Public Access settings to align with security policies and regulatory requirements.
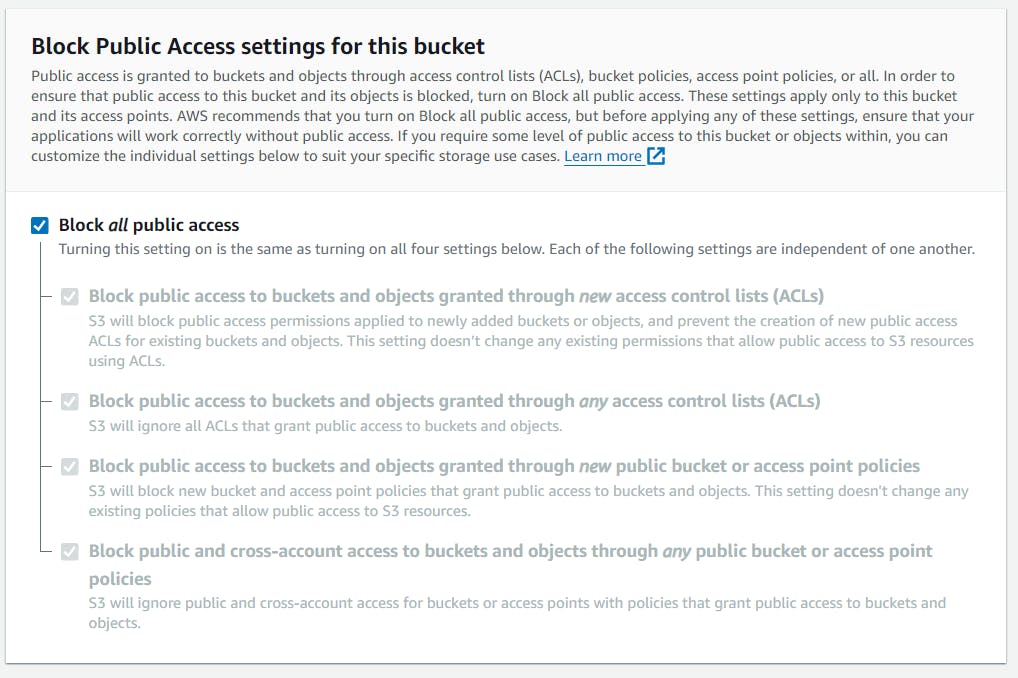
By utilizing Bucket settings for Block Public Access effectively, you can bolster the security of your S3 buckets and mitigate the risk of unauthorized data exposure.
Amazon S3 – Encryption
Amazon S3 provides robust encryption mechanisms to ensure the security and confidentiality of data stored in its buckets. There are two primary methods of encryption:
Server-Side Encryption (SSE):
Server-Side Encryption involves encrypting data at the server level before saving it to disk.
There are three options for SSE:
SSE-S3 (Default):
Amazon S3 automatically encrypts objects using AES-256 encryption before storing them on disk.
SSE-S3 is the default encryption method, ensuring that all objects uploaded to S3 buckets are encrypted by default.
This encryption is transparent to users, and decryption occurs automatically when accessing the data.
SSE-KMS (Key Management Service):
SSE-KMS allows you to use AWS Key Management Service (KMS) to manage encryption keys securely.
With SSE-KMS, you have greater control over key management, including key rotation, auditing, and access control.
You can define fine-grained access policies for encryption keys, allowing specific IAM users or roles to encrypt or decrypt objects.
SSE-C (Customer-Provided Keys):
SSE-C allows you to provide your encryption keys to Amazon S3 when uploading objects.
With SSE-C, Amazon S3 manages the encryption process but uses the customer-provided keys to encrypt and decrypt data.
This option provides additional control over encryption keys, allowing you to manage key lifecycle independently.
Use Cases:
Protecting sensitive data stored in S3 buckets from unauthorized access.
Ensuring compliance with data protection regulations and industry standards.
Client-Side Encryption:
Client-Side Encryption involves encrypting data on the client-side before uploading it to Amazon S3. This gives users complete control over the encryption process and keys.
Description: With client-side encryption, data is encrypted on the client-side using encryption libraries or tools before being uploaded to S3 buckets.
Key Management: Users are responsible for managing encryption keys securely and ensuring that only authorized parties have access to the keys.
Secure Transmission: Encrypted data is transmitted over secure channels (such as HTTPS) to Amazon S3, where it is stored encrypted.
Decryption: To access encrypted data, users must decrypt it using the appropriate decryption keys. S3 does not have access to the decryption keys or plaintext data.
Use Cases:
Providing an additional layer of security for highly sensitive data.
Allowing users to retain full control over encryption keys and data access.
Step-by-Step Guide: S3 Bucket Policy Creation
Explore this comprehensive tutorial for detailed instructions on crafting a bucket policy in Amazon S3 to enable public access to files: AWS S3 Bucket Policy Hands-On: A Step-by-Step Guide
Summary:
Amazon S3 offers robust security features, including encryption, access control, and IAM integration.
User-Based Security: IAM allows defining policies for users or roles, controlling their actions.
Resource-Based Security: Resource policies determine access rules for IAM principals and other AWS accounts.
Use Cases: S3 bucket policies enable various scenarios, including hosting websites and granting access.
Block Public Access: Prevents accidental data exposure by blocking public access to bucket policies and ACLs.
Encryption:
Server-Side Encryption ensures data stored in S3 is encrypted at rest.
Client-Side Encryption provides an additional layer of security.
Step-by-Step Guide: Follow the tutorial to create a bucket policy in S3 for enabling public access.

